Phishing is a scam in which the attacker sends an email purporting to be from a valid financial or eCommerce provider. The email often uses fear tactics in an effort to entice the intended victim into visiting a fraudulent website.
Phishing is a scam in which the attacker sends an email purporting to be from a valid financial or eCommerce provider. The email often uses fear tactics in an effort to entice the intended victim into visiting a fraudulent website. 
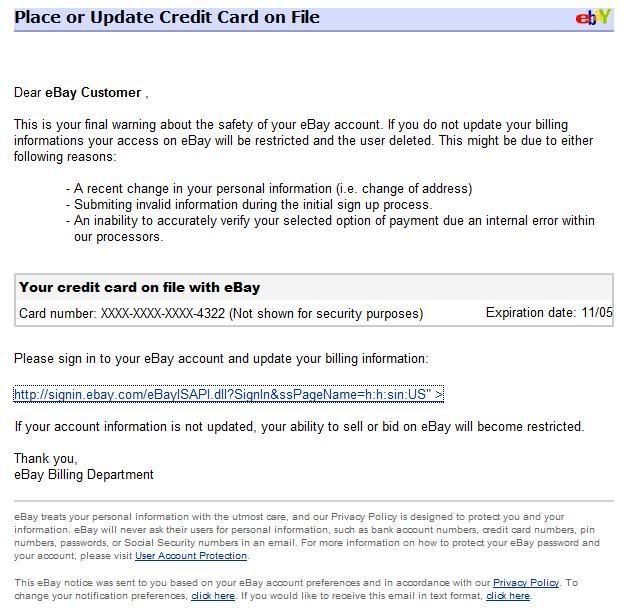
eBay phishing scam
This eBay phishing email includes the eBay logo in an attempt to gain credibility. The email warns that a billing error may have been made on the account and urges the eBay member to login and verify the charges.
Scammers phish on ebay to obtain eBay ID's which then are used to sell fake or non-existent goods or such accounts can be sold further in the underground market. In other words, the new owners of stolen eBay ID's now are equipped with positive feedback, previously generated by the real owner, and are now used to scam people.
Look at the link here. It looks as valid as it could. It is written http://signin.ebay.com, but this written link actually points again, yes, to a clone of ebay. This is done with a href code in html coding. I will show you an example. Click on this link:
http://www.ebay.com
The Address shows ebay, but you were linked to amazon. I have linked you to amazon, but Con artist will link you to dupes of legit business websites and scam you. Beware what you click, your browser shows you the link in the left bottom corner if you only point over the link, without clicking it.
Find out more in http://www.bustathief.com/2007/08/what-is-phishing-ebay-phishing-examples.html

Another example of phishing is Paypal. Paypal is becoming the online payment processor of choice for many users. Paypal allows virtually anyone to except credit card payments. Paypal is also a great way to send and receive electronic payments. Unfortunate fame has it’s price and in the case of Paypal that means scam artists preying on the Paypal members.
The most common Paypal Scam involves e-mail. You will receive an e-mail from someone claiming to be Paypal requesting you verify your information. Look out for warning signs below to identify phishing scam:
Warning Sign1 : Paypal will never send you an E-Mail Requesting Your Personal Information
Warning Sign2 : Often this e-mail will be sent to an e-mail address that is not the same one that Paypal has on file.
Warning Sign3: Forged Headers (from address). This is often hard to detect without knowledge of the Internet. Many spam filters are now setup to block e-mail that has forged headers. Ask your e-mail provider how you can block Forged Headers.
Warning Sign4: Greetings. Paypal knows who you are they will use the name you registered with.
Warning Sign5: Threats. The e-mail will threaten to suspend your account if you don’t take immediate action.
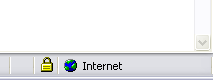
Warning Sign6: Non Secure Page. If you do click on the link in the E-Mail you will not be on a secure Page, No Https in the URL and no little Padlock in the lower left hand corner of your browser.
Warning Sign7: Bad Grammar or Misspelled words
If you receive an E-mail from Paypal with even 1 of these warning signs more likely it is a scam.
There are several different techniques to combat phishing, including legislation and technology created specifically to protect against phishing.
One strategy for combating phishing is to train people to recognize phishing attempts, and to deal with them. Education can be promising, especially where training provides direct feedback. People can take steps to avoid phishing attempts by slightly modifying their browsing habits. When contacted about an account needing to be "verified" (or any other topic used by phishers), it is a sensible precaution to contact the company from which the e-mail apparently originates to check that the e-mail is legitimate. Alternatively, the address that the individual knows is the company's genuine website can be typed into the address bar of the browser, rather than trusting any hyperlinks in the suspected phishing message.
1. Helping to identify legitimate sites
Some anti-phishing toolbars display the domain name for the visited website. The petname extension for Firefox lets users type in their own labels for websites, so they can later recognize when they have returned to the site. If the site is suspect, then the software may either warn the user or block the site outright.
2. Browsers alerting users to fraudulent websites
Another popular approach to fighting phishing is to maintain a list of known phishing sites and to check websites against the list. Microsoft's IE7 browser, Mozilla Firefox 2.0, and Opera all contain this type of anti-phishing measure. Firefox 2 uses Google anti-phishing software. Opera 9.1 uses live blacklists from PhishTank and GeoTrust, as well as live whitelists from GeoTrust. Some implementations of this approach send the visited URLs to a central service to be checked, which has raised concerns about privacy.
3. Eliminating phishing mail
Specialized spam filters can reduce the number of phishing e-mails that reach their addressees' inboxes. These approaches rely on machine learning and natural language processing approaches to classify phishing e-mails.
Many of these phishing emails appear to be quite legitimate. Don't be a victim. Look over the following examples of phishing scams to familiarize yourself with the clever techniques used.